May 15, 2017 (LBO) – Sri Lanka Computer Emergency Response Team today said incidents of local computer systems being affected by the recent ransomware virus have not been reported to them so far.
Chief Information Security Engineer Roshan Chandraguptha told Lanka Business Online that it is essential to follow precautionary measures to avoid such attack.
“So far we haven’t received any reports of an infected computer in Sri Lanka. It has so far no effect on the financial system either,” Chandraguptha said.
“Updating Windows is the best way to avoid this. People can report to us, if there is a known attack of ransomware virus.”
Due to Vesak holidays, computer systems in the private and public sector were mostly not used during the past few days reducing risk of infection with the virus.
Sri Lanka Computer Emergency Readiness Team however informed the public to be on high level alert for this malicious software.
Software security companies said the ransomware worm called "WannaCry" has infected computer systems in over 100 countries with Russia, Ukraine, and Taiwan being the top targets, since Friday.
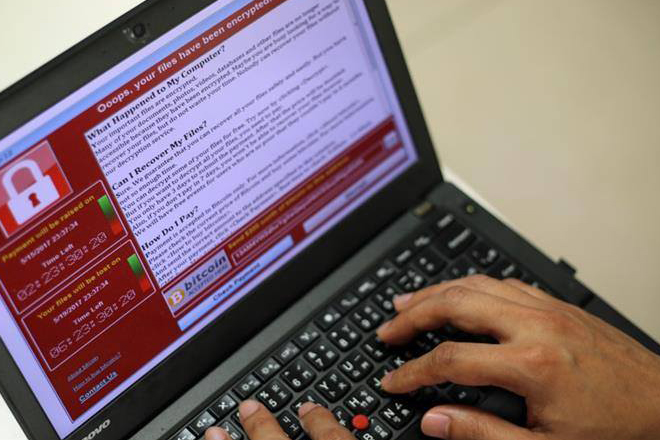
WannaCry is a form of ransomware that locks up files on a computer and encrypts them in a way that cannot access them anymore.
It targets Microsoft's widely used Windows operating system including Windows XP, Windows Vista, Windows 7, Windows 8 and Windows 10 systems.
On March 14, Microsoft released a security update to patch this vulnerability and protect customers.
“We are among the first responders to attacks on the internet and we’re working comprehensively to address cybersecurity threats,” Brad Smith, President and Chief Legal Officer at Microsoft said.
“In this instance, this included the development and release of the patch in March, a prompt update on Friday to Windows Defender to detect the WannaCrypt attack.”
While this new update protected newer Windows systems, many computers remained unpatched globally.
The hack forced British hospitals to turn away patients, affected Spanish companies such as Telefonica, and threw other government agencies and businesses into chaos.
When a system is infected, a pop-up window appears with instructions on how to pay a ransom amount of 300 US dollars and the payment is only accepted in bitcoin.
The pop-up also features two countdown clocks; one showing a three-day deadline before the ransom amount doubles to 600 dollars, another showing a deadline of when the target will lose its data forever.
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the US' National Security Agency, according to cyber-security providers.
Solutions/Workarounds
The effected PCs should be immediately disconnected from the network.
Contact your virus guard providers or security vendors for necessary actions.
Email attachments should be blocked relating to following files but not limited to pdf, javascript, doc, macro based Microsoft word or related executables.
Prevention:
• Have all files backed up in a completely separate system.
• This ransomware targets all versions of Windows including Windows XP, Windows Vista, Windows 7, Windows 8 and Windows 10.
• Clients should ensure that they are patched on MS17-010.
• Disable the outdated protocol SMBv1.
• Isolate unpatched systems from the larger network Recovery:
• As of now, there are no know recovery methods available.
• Do not try to pay the ransom
• Ensure you have smart screen (in Internet Explorer) turned on, which helps identify reported phishing and malware websites and helps you make informed decisions about downloads
• Have a pop-up blocker running on your web browser
• Regularly backup your important files